Dealing with Real-Time Attacks on User Accounts
(suomeksi alla)
The Holy Grail of cybersecurity defense is to effectively deal with real-time attacks. In most attacks on MFA protected user accounts, the attack method is divided into two parts: the active phishing phase and the exploitation phase. This scenario does not require real-time actions from the attacker and well protected authentication services can prevent these attacks in real-time by properly configuring the services. This is no longer the case for new real-time attacks on passwordless mobile MFA’s using PKI certificates (Mobiilivarmenne).
We have witnessed throughout this year 2025 that attackers have been exploiting the Mobiilivarmenne mechanism, where a SIM-based Mobile Certificate provides passwordless authentication to corporate users and consumers. The attacks may appear crude, but they are an effective way to piggy-back the user authentication process in real-time. Unlike session cookie-theft attacks against SMS or app-based MFA, there are no reusable session tokens in a PKI-based authentication process. Instead, criminals phish victims into authorizing fraudulent transactions by relaying their identification inputs into a fake website, such as a fake-Omakanta, to a real service in the moment, most likely an instant-credit lending site.
Victims are phished using SMS or email links that are directed to a fake login page where they enter their phone number and ID. The attacker then initiates a genuine mobile PKI certificate authentication with a real instant-credit lending site. The victim’s phone shows a legitimate PKI signing consent prompt, but this message may be framed by the attacker’s message talking about a mobile certificate update or similar. As the victim enters their PIN, the digital signature is used by the attacker to complete the financial fraud in the actual instant credit website, while the victim is duped into thinking that he/she is accessing a different site, such as Omakanta.
The victims will receive warnings and mismatched service names may appear in the consent dialog, but in a successful phishing attack and under social-engineering pressure, many victims ignore these messages.
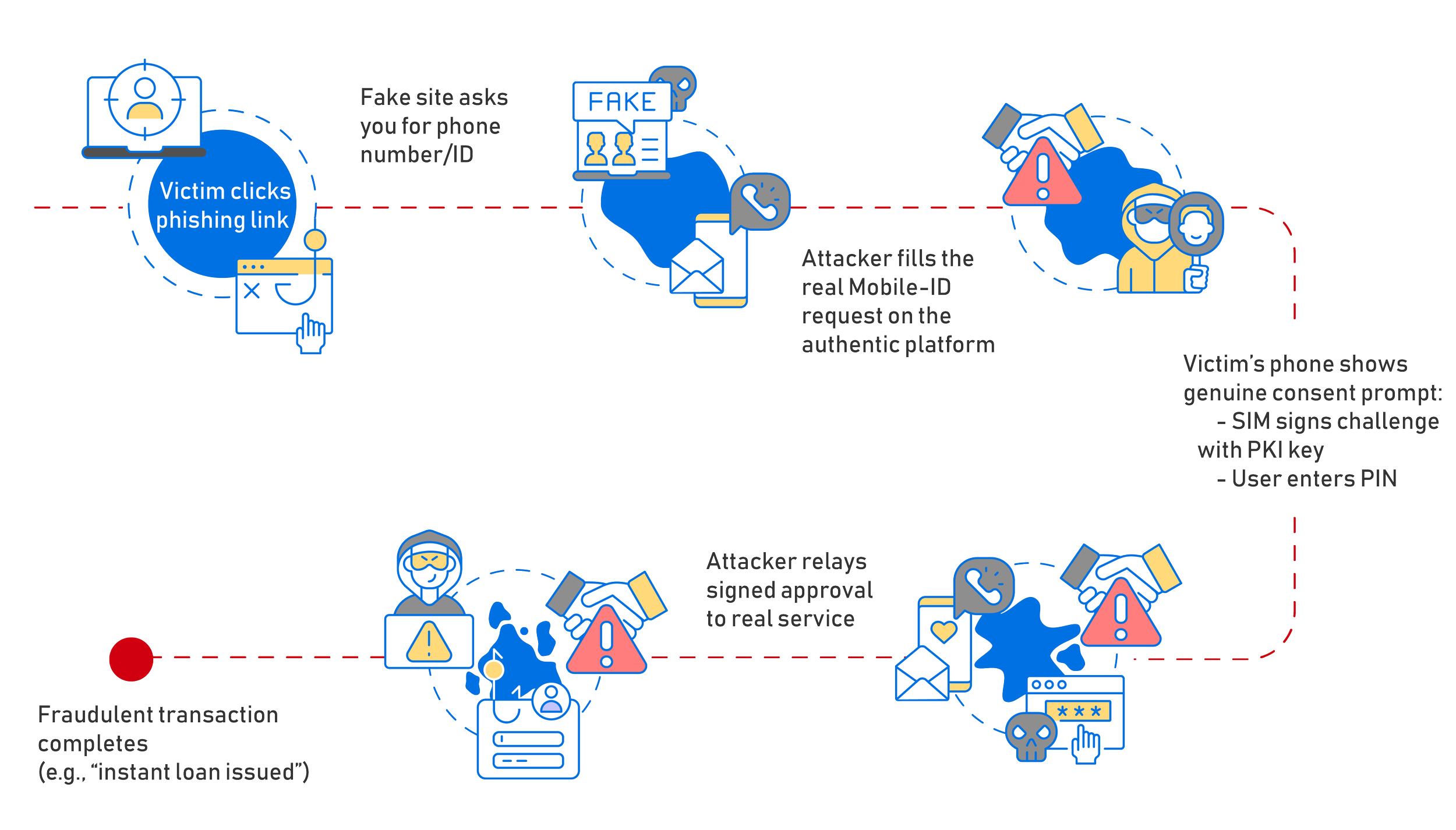
A Step-by-Step Attack Flow:
[1] Victim clicks phishing link
[2] Fake site asks for phone number/ID
[3] Attacker initiates real Mobile-ID request
[4] Victim’s phone shows genuine consent prompt
- SIM signs challenge with PKI key
- User enters PIN
[5] Attacker relays signed approval to real service
[6] Fraudulent transaction completes
(e.g., instant loan issued)
The key point in this attack is that everything after Step 3 is genuine cryptography: the SIM card-based PKI key and signature are valid. The weakness the attacker exploits, lies in the context text shown to the user and the victim's ability to notice when it doesn’t match the expected service. But the real challenge in all this, is that the attack happens in real-time, where ordinary cybersecurity defenses cannot protect the victim.
While there are several tasks that the victim can perform to defend oneself from this attack, the common advice often depends on the victim's ability to effectively counter advanced cyber-threats. This is not a bullet-proof solution as victims of phishing attacks are no technical experts on mobile authentication. A bullet-proof solution, is a hardware-based FIDO2 security key, which resist all adversary-in-the-middle and phishing attacks in real-time.
A hardware-based FIDO2 security key (SpearID FIDO2) is immune to real-time piggy-back attacks because it cryptographically binds the authentication consent signature to the service provider's real internet domain (example google.com). If the victim is directed a fake website, the authenticator will generate an authentication challenge tied to fake website and not the real website the victim belief he/she is accessing. In this case, even if the attacker relays the victim’s identification inputs, the authentication consent signature simply won’t validate at the real website since this was not bound to it. Unlike mobile PKI (Mobiilivarmenne), where the PKI certificate in the SIM card is used to sign whatever text is provided by the web service, FIDO2 enforces origin-binding at the protocol level. The victim is technically barred from authenticating to a real website via a fraudulent website, and this despite any phishing scheme. This is why Microsoft and other industry leaders classify FIDO2 passkeys as phishing-resistant MFA.
The only effective and easy way to deal with real-time attacks on user accounts is to adopt truly phishing FIDO2 security keys. Get a SpearID FIDO2 security key now.
Käyttäjätilien reaaliaikaisiin hyökkäyksiin vastaaminen
Kyberturvallisuuden Graalin malja on tehokas reagointi reaaliaikaisiin hyökkäyksiin. Useimmissa MFA-suojatuille käyttäjätileille kohdistuvissa hyökkäyksissä hyökkäysmenetelmä jakautuu kahteen osaan: aktiiviseen kalastelu-vaiheeseen ja hyödyntämisvaiheeseen. Tämä skenaario ei vaadi hyökkääjältä reaaliaikaisia toimia, ja hyvin suojatut todennuspalvelut voivat estää nämä hyökkäykset reaaliajassa konfiguroimalla palvelut oikein. Tämä ei enää päde uusiin reaaliaikaisiin hyökkäyksiin, jotka kohdistuvat salasanattomiin mobiili-MFA-palveluihin, joissa käytetään PKI-varmenteita (Mobiilivarmenne).
Olemme havainneet vuoden 2025 aikana, että hyökkääjät ovat hyödyntäneet Mobiilivarmenne-mekanismia, jossa SIM-pohjainen mobiilisertifikaatti tarjoaa salasanattoman todennuksen yrityskäyttäjille ja kuluttajille. Hyökkäykset saattavat vaikuttaa karkeilta, mutta ne ovat tehokas tapa hyödyntää käyttäjän todennusprosessia reaaliajassa. Toisin kuin SMS- tai sovelluspohjaista MFA:ta vastaan tehdyt istuntokohtaisten evästeiden varastamishyökkäykset, PKI-pohjaisessa todennusprosessissa ei ole uudelleenkäytettäviä istuntotunnuksia. Sen sijaan rikolliset huijaavat uhreja valtuuttamaan petollisia maksutapahtumia välittämällä uhrien väärennetylle verkkosivustolle, kuten väärennetylle Omakanta-sivustolle, syöttämät tunnistetietonsa, todelliseen palveluun, todennäköisesti pikaluottosivustolle.
Uhrit huijataan tekstiviesteillä tai sähköpostilinkkeillä, jotka ohjaavat heidät väärennetylle kirjautumissivulle, jossa he syöttävät puhelinnumeronsa ja tunnuksensa. Hyökkääjä käynnistää sitten aidon mobiilin PKI-varmenteen todennuksen todellisella pikaluottosivustolla. Uhrin puhelimeen tulee laillinen PKI-allekirjoituksen suostumuspyyntö, mutta tämä viesti voi olla kehystetty hyökkääjän viestillä, jossa kerrotaan mobiilisertifikaatin päivityksestä tai vastaavasta. Kun uhri syöttää PIN-koodinsa, hyökkääjä käyttää digitaalista allekirjoitusta suorittaakseen taloudellisen petoksen todellisella pikaluottosivustolla, kun taas uhri luulee käyttävänsä eri sivustoa, kuten Omakantaa.
Uhrit saavat varoituksia, ja suostumusikkunassa saattaa näkyä virheellisiä palvelunimiä, mutta onnistuneessa tietojenkalasteluyrityksessä ja sosiaalisen manipuloinnin paineessa monet uhrit sivuuttavat nämä varoitukset.
Hyökkäysprosessi vaiheittain:
[1] Uhri klikkaa kalastelu-linkkiä.
[2] Huijaussivusto pyytää puhelinnumeroa/tunnusta.
[3] Hyökkääjä käynnistää aidon Mobile-ID-pyynnön
[4] Uhrin puhelimeen tulee aito suostumuspyyntö
- SIM allekirjoittaa haasteen PKI-avaimella
- Käyttäjä syöttää PIN-koodin
[5] Hyökkääjä välittää allekirjoitetun hyväksynnän aitoon palveluun
[6] Petollinen tapahtuma suoritetaan loppuun
(esim. välitön laina myönnetään)
Tämän hyökkäyksen avaintekijä on, että kaikki vaihe 3:n jälkeen on aitoa salausta: SIM-korttiin perustuva PKI-avain ja allekirjoitus ovat kelvollisia. Hyökkääjän hyödyntämä heikkous piilee käyttäjälle näytetyssä kontekstitekstissä ja uhrin kyvyssä huomata, kun se ei vastaa odotettua palvelua. Todellinen haaste tässä kaikessa on kuitenkin se, että hyökkäys tapahtuu reaaliajassa, jolloin tavalliset kyberturvallisuuspuolustukset eivät pysty suojelemaan uhria.
Vaikka uhri voi suorittaa useita tehtäviä puolustautuakseen tätä hyökkäystä vastaan, yleiset neuvot riippuvat usein uhrin kyvystä torjua tehokkaasti kehittyneitä kyberuhkia. Tämä ei ole luotettava ratkaisu, koska kalastelu-hyökkäysten uhrit eivät ole mobiilitodennuksen teknisiä asiantuntijoita.
Luotettava ratkaisu on laitteistopohjainen FIDO2-turva-avain, joka torjuu kaikki välittäjähyökkäykset ja kalastelu-hyökkäykset reaaliajassa.
Laitteistopohjainen FIDO2-turva-avain (SpearID FIDO2) on immuuni reaaliaikaisille piggy-back-hyökkäyksille, koska se sitoo salakirjoituksella todennuslupasignatuurin palveluntarjoajan todelliseen internet-verkkotunnukseen (esimerkiksi google.com). Jos uhri ohjataan väärennetylle verkkosivustolle, todennuslaite luo todennushaasteen, joka liittyy väärennettyyn verkkosivustoon eikä todelliseen verkkosivustoon, johon uhri uskoo olevansa yhteydessä. Tässä tapauksessa, vaikka hyökkääjä välittäisikin uhrin tunnistetiedot, todentamisen suostumuksen allekirjoitus ei yksinkertaisesti kelpaa todellisella verkkosivustolla, koska se ei ole sidottu siihen. Toisin kuin Mobiilivarmenne, jossa SIM-kortin PKI-varmennetta käytetään allekirjoittamaan mikä tahansa verkkopalvelun toimittama teksti, FIDO2 pakottaa alkuperäsidonnan protokollatasolla. Uhri ei voi teknisesti todentaa itseään oikealle verkkosivustolle väärennetyn verkkosivuston kautta, huolimatta kalastelu-huijauksista. Siksi Microsoft ja muut alan johtajat luokittelevat FIDO2-salasanat kalastelun kestäviksi MFA-todentamismenetelmiksi.
Ainoa tehokas ja helppo tapa torjua käyttäjätileihin kohdistuvia reaaliaikaisia hyökkäyksiä on ottaa käyttöön aidot FIDO2-turva-avaimet. Hanki SpearID FIDO2 -turva-avain nyt.